3.5 Storage
How you Store and Secure your research data safeguards your research investment
If you want access to your data in the future in order to reproduce the findings, or to augment subsequent research, or establish a precedent, storage and security will play a major role in it.
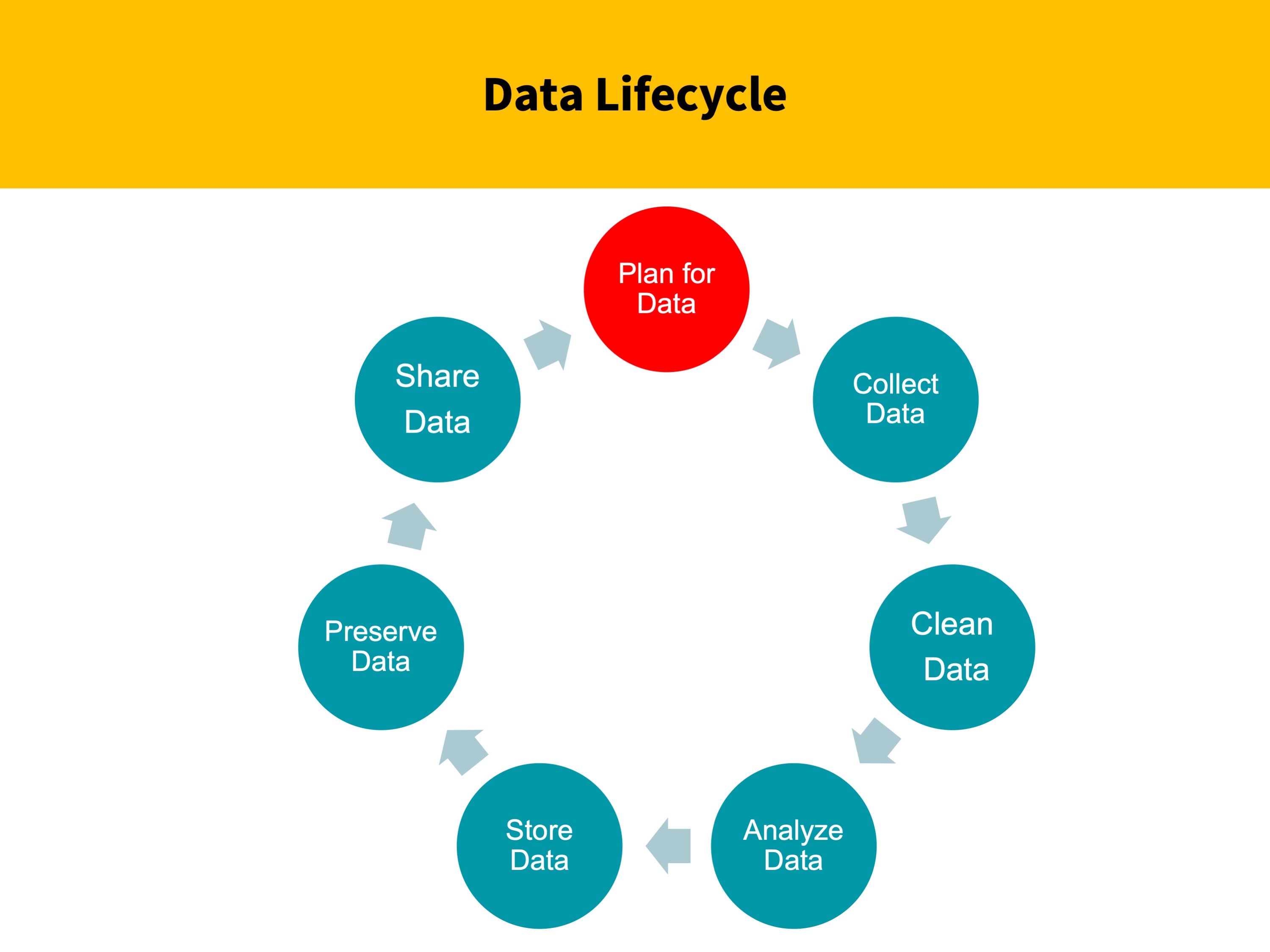
When should you be thinking about storage of data? During every stage of the research cycle.
Tracking and documenting where your data is and will be stored at different stages of the cycle will be a key differentiator in meeting your data management goals. Especially when you have a team working with you.
More people = more entropy
3.5.1 Storage Solutions at UMB

Primary Storage option: Office 365 – One Drive – 5TB space that is secure, universally accessible storage for working files. It is HIPPA and FERPA (Family Educational Rights and Privacy Act) compliant
Network storage in your department. I, K, J,…. drives
Backup Storage option: SOMFiles PI’s from across campus w/ research funding can receive up to 1TB of free backup storage for research data – Additional space can be purchased.
Check with your school and dept IT to find out what storage and back up solutions exist for you.
3.5.2 Cloud Storage Options

Cloud storage is amazing we can all agree. Universal access, Ease of transfer of data across computing environments and it is quickly becoming a primary storage option for many researchers. (inexpensive, less prone to disaster, less space)
Remember to avoid cloud storage options that can take ownership of your data
Important! If you are working with human subjects, make sure the storage is HIPAA compliant.
Always have a backup and make sure your data is safely secure in another storage solution.
On our campus, the main solution is now SharePoint and OneDrive.
3.5.3 Backup Considerations

What about backing up your data?
How will you respond to a loss of data? It could happen and does!
Data loss is caused by hardware failure, software failure, lost drives, theft, or even environmental disasters (including human error).
Store your critical data files in a centralized location with a plan to back it up routinely
Stay away from using laptops and flash drives for the master copy of your data. They are easily lost, stolen, or damaged.
Here are a few questions you might need to consider during the data management planning process.

Also consider saving multiple copies of your data and dispersing them geographically.
Dispersing data will protect it from hardware/software failure and environmental disasters.
Remembering The 3-2-1 principle of backup makes it easy to remember: Have 3 copies of your files on at least 2 different media with 1 off site.
3.5.4 Security Considerations

Certain types of data require special security considerations, and not only Protected Health Information (PHI)! Remember to work with your IT department and the human research protection office to understand extra steps that will keep your data safe.
Human subjects research data must be kept secure in a way that is HIPAA compliant.
Patents or commercial data must be secure from theft or damage
You work hard to collect your data, If you are concerned about the intellectual property of your data, you should be taking steps to make sure it is secure when storing it.
You should always make sure the IT department is providing antivirus software that is up-to-date and has put measures in place to encrypt the data or your PC.
On your own, there are several things you can do, including:
Adding passwords to files or folders
Locking unused machines in your lab or office (work with IT)
Have other researchers who work with your data sign use agreements. To make sure that your collaborators are held accountable for what they do with the data. Might require them not to store data on a mobile device, for example.
Do not store or transmit sensitive data without encryption!
SecureXfer can be used for secure file transfer on campus, rather than sending via email. It is free, works for large files, and can be used by all on campus. Files are deleted within 2 weeks.